Email Proofs Architecture
Email proof sequence flow
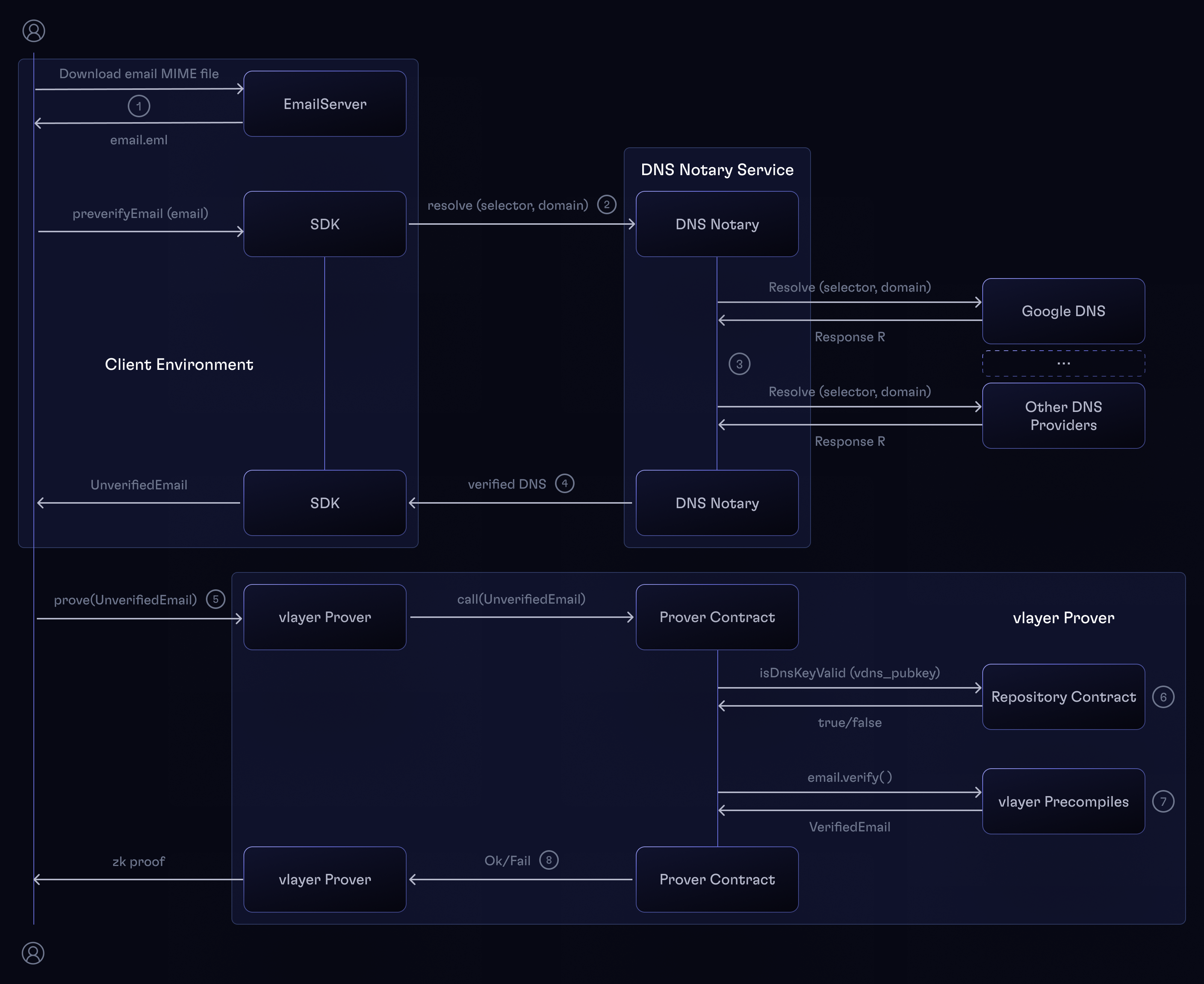
Generating and ZK-proving an Email Proof consists of the following steps:
- The received email MIME file is extracted from the email client.
- The
preverifyEmailin the SDK prepares theUnverifiedEmailstruct that is ready to be sent to the Prover Contract.- Performs basic preverification - checks if the
DKIM-Signatureheader is present. - Calls the
DNS Notaryto get the verification data of the sender's domain. - Note that all these steps can be performed without the
vlayerSDK.
- Performs basic preverification - checks if the
- The
DNS Notaryfetches the public key used to sign the email from a number of DNS providers, compares the results, and if there's a consensus among them, signs the result with its private key. - The DNS record with it's signature and the raw email together form the
UnverifiedEmailstruct. - A
v_callis made to the vlayer server with theUnverifiedEmailstruct as well as the rest of the Prover contract arguments as calldata, chain ID, and the address of the deployed Prover contract. - The Prover contract must use the
EmailProofLib, where theDNS Notarypublic key is verified. TheEmailProofLiblibrary calls theRepositorycontract to verify whether theDNS Notarypublic key is valid. It also checks the signature TTL against the current block timestamp. - Next, the
EmailProofLibcontract calls theemail_proof.verify(UnverifiedEmail)custom precompile (see Precompiles), which validates the Email Proof, parses the email MIME file, and returns aVerifiedEmail. - If the verification is successful, the
EmailProofLibreturns theVerifiedEmailstruct to the Prover contract. Otherwise, it will revert.